Connectivity
Connectivity (Cont'd). A second way
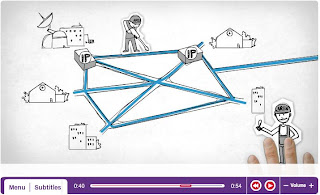
in which a set of computers can be indirectly connected is shown in Figure
interconnection network. In this situation, a set of independent networks
(clouds) are interconnected to form an internetwork,
or internet for short. We adopt the Internet’s convention of referring to a
generic internetwork of networks as a lowercase i
internet, and the currently operational
TCP/IP Internet as the capital I Internet. A node that is connected to two or more networks is commonly called a router or gateway, and it plays much
the same role as a switch—it forwards messages from
one network to another. Note that an internet
can itself be viewed as another kind of network, which means that an internet can be built from an interconnection of internets.
Thus, we can recursively build arbitrarily
large networks by interconnecting clouds to form larger clouds.
 |
| Interconnection Networks |
Just
because a set of hosts are directly or indirectly connected to each other does not
mean that we have succeeded in providing host-to-host connectivity. The final requirement
is that each node must be able to say which of the other nodes on the network
it wants to communicate with. This is done by assigning an address to each node. An address is a
byte string that identifies a node; that is, the network can use a node’s
address to distinguish it from the other nodes connected to the network. When a
source node wants the network to deliver a message to a certain destination node,
it specifies the address of the destination node. If the sending and receiving nodes
are not directly connected, then the switches and routers of the network use
this address to decide how to forward the message toward the destination. The
process of determining systematically how to forward messages toward the
destination node based on its address is called routing.
This
brief introduction to addressing and routing has presumed that the source node
wants to send a message to a single destination node (unicast). While this is the most common
scenario, it is also possible that the source node might want to broadcast a message to all the
nodes on the network. Or a source node might want to send a message to some
subset of the other nodes, but not all of them, a situation called multicast. Thus, in addition
to node-specific addresses, another requirement of a network is that it support
multicast and broadcast addresses.
The main idea to take away from
this discussion is that we can define a network recursively as consisting of two or more nodes connected by a
physical link, or as two or more networks connected by a node. In other words, a network can
be constructed from a nesting of networks, where at the bottom level, the network
is implemented by some physical medium. One of the key challenges in providing
network connectivity is to define an address for each node that is reachable on
the network (including support for broadcast and multicast connectivity), and to be able to use
this address to route messages toward the appropriate destination node(s).